Contact us today discover how our products services solutions combine to work for you. The methods of data intake storage access and disposal are all considered in developing a WISP that addresses how at each point sensitive.
 Managing Data Security In A Small Organisation
Managing Data Security In A Small Organisation
Full report available to GigaOm Subscribers.

Managing data protection. Part of a proactive approach to data risk management is the creation of a written information security plan WISP a document that outlines data security methodologies for the organization and gives users insight into their role in data protection. 1 the nature of the datainformation at issue eg does the supplier process sensitive special category data or financial data or more low risk personal data such as employee email addresses 2 the service offered by the supplier and how it uses the customers data 3 the committed revenue. Make the move to Deloittes Managed Data Protection.
Typically a negotiated deal will result in the parties agreeing some form of middle ground based on. Organizations must prioritize data security management and place it on an equal footing with traditional information and network security. Adequately protecting data is one of the most challenging aspects of data management.
Protecting sensitive app data on end-users devices. Ad A Better Alternative To Whitebox Crypto Solutions. Quick to deploy and easy to integrate.
Ad Achieve faster more flexible recovery and retention options. Subscribe to GigaOm Research. Secure ransomware protection and unprecedented resiliency for any size business.
Data protection is the process of preserving datas confidentiality integrity and availability. Data availability and data management. Microsoft Security Provides Integrated Security with Full Coverage.
End-user recovery allows the end-user to use the Previous Version tab of a shared folder or file to recover the data from a protected computer without the Administrator intervention. Ad Achieve faster more flexible recovery and retention options. When the University acquires utilizes maintains or accesses data it takes on an obligation to protect that data.
Ad Industry leaders in Parental Control Employee Monitoring software for 14 years. Given the value of data today data protection is often the driver that propels an enterprise toward new levels of excellence in managing risk. Ad Gear up for growth as remote working becomes the next normal ensuring you stay connected.
Request your Talend demo now to learn more. Although data protection management refers to the best practices an organization applies to managing data protection applications and operations its also a technology and product category with both backup and systems management application vendors providing software that specifically addresses data protection. Data protection strategies are evolving along two lines.
Data availability ensures users have the data they need to conduct business even if the data. 25 Managing Data Protection Set up data loss prevention DLP for applications that support this feature. Managing data protection security and compliance in the hybrid cloud Hybrid cloud answers the toughest questions around security data protection and compliance in the cloud but only with the.
Request demo or download product sheet. Ad Strengthen and Streamline Cybersecurity Across Multiplatform Environments. Secure ransomware protection and unprecedented resiliency for any size business.
If you have not registered yet you will need your Customer Support Identifier CSI in order to. Red Hats end-to-end approach to Kubernetes and data management enables users to protect data across multiple environments while providing a consistent set of enterprise-grade data services to accelerate data mobility migrations and disaster recovery. In order to allow users to recovery their data through Previous Versions we have to extend the Active Directory Schema after that we can enable it and install the Shadow Copy client on the workstations.
Ad Protect your Video DVDs from being copied. View manage and take full control over your users computer and Internet activities. Ad See how Talend can simplify all your data management needs.
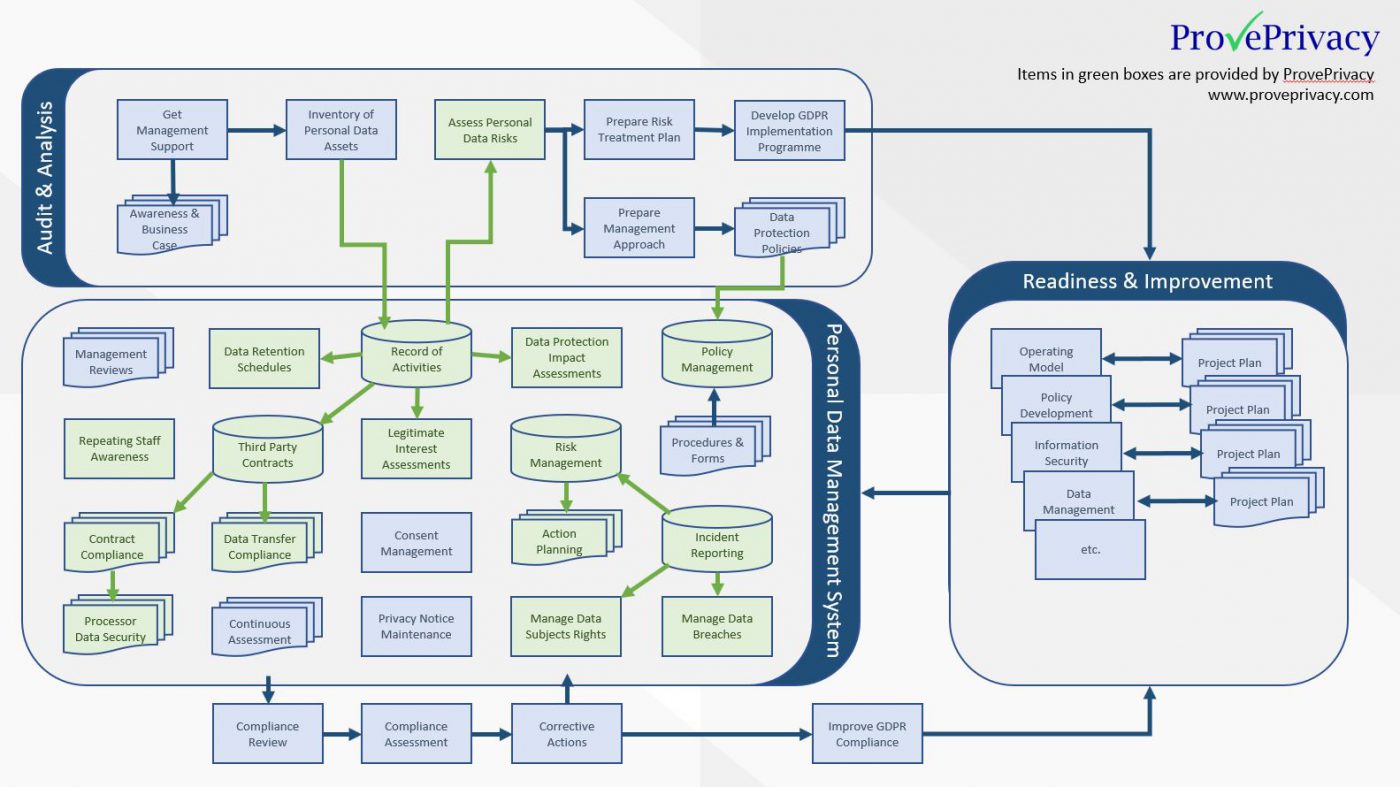 Implementing A Personal Data Management System Proveprivacy
Implementing A Personal Data Management System Proveprivacy
 Data Privacy Guide Definitions Explanations And Legislation Varonis
Data Privacy Guide Definitions Explanations And Legislation Varonis
 Managing Data Protection By 1 Mrs Pravina Dodah
Managing Data Protection By 1 Mrs Pravina Dodah
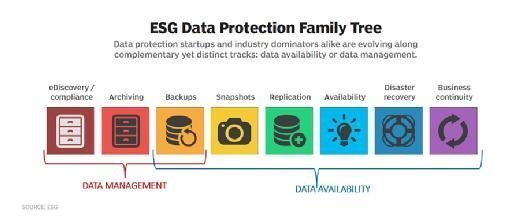 What Is Data Protection And Why Is It Important Definition From Whatis Com
What Is Data Protection And Why Is It Important Definition From Whatis Com
 Data Protection And Privacy Management System
Data Protection And Privacy Management System
 What Is Data Protection And Why Is It Important Definition From Whatis Com
What Is Data Protection And Why Is It Important Definition From Whatis Com
 Managed Data Protection Services
Managed Data Protection Services
 Managing Personal Data Protection From Small To Large Enterprise Perspective Youtube
Managing Personal Data Protection From Small To Large Enterprise Perspective Youtube
 Managing Data Protection Security And Compliance In The Hybrid Cloud Cio
Managing Data Protection Security And Compliance In The Hybrid Cloud Cio
 Managing Data Protection 9780852993668 Amazon Com Books
Managing Data Protection 9780852993668 Amazon Com Books
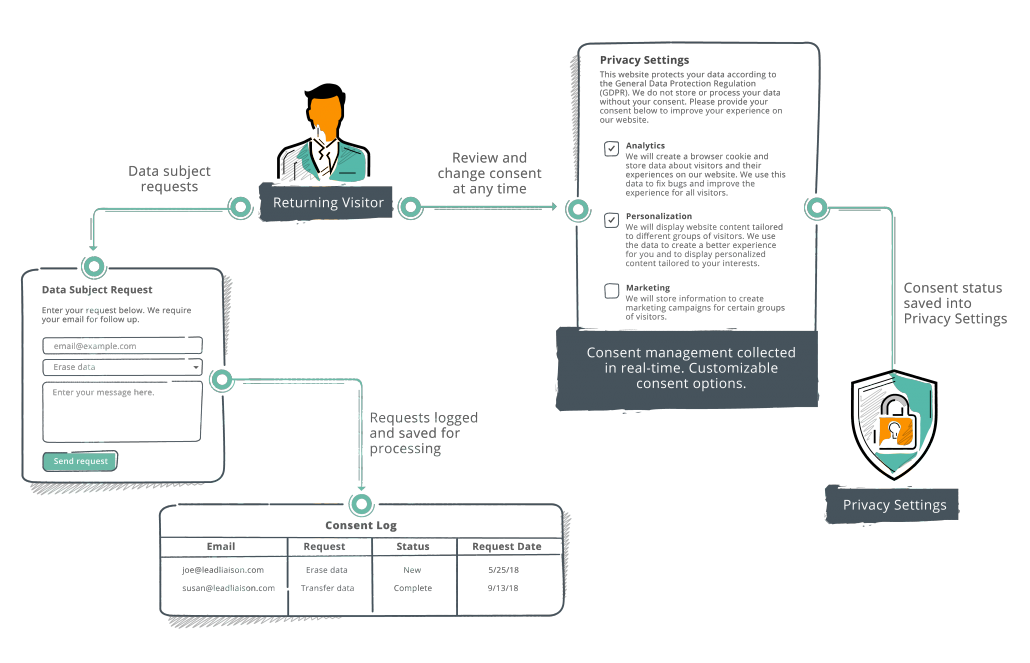 Gdpr Consent Management And Data Subject Request Solutions
Gdpr Consent Management And Data Subject Request Solutions
 Managing Data Privacy In The Age Of Digital Transformation
Managing Data Privacy In The Age Of Digital Transformation
 Managing Data Protection By 1 Mrs Pravina Dodah
Managing Data Protection By 1 Mrs Pravina Dodah
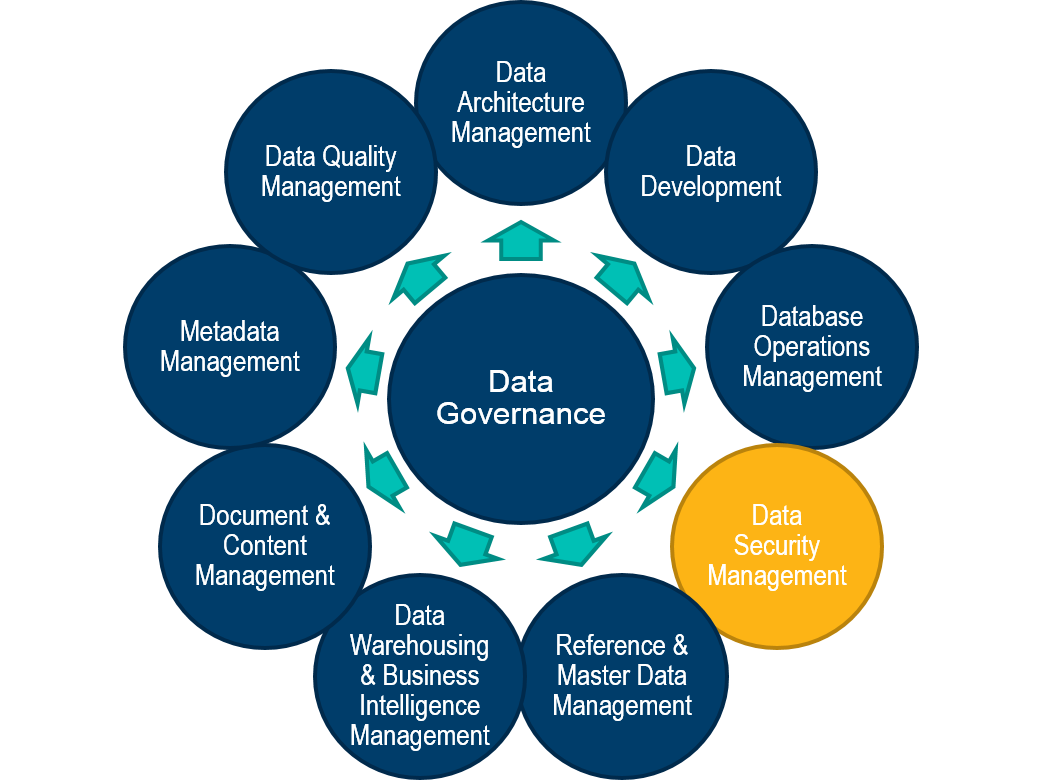

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.